Why Passkeys and Security Keys are considered un-phishable and more secure than Authenticator Apps like Google Authenticator
The article below does a very good job of explaining U2F (Hardware Security Keys) vs. OTP (Google Authenticator and similar Authenticator Apps).
Bypassing LastPass’s “Advanced” YubiKey MFA: A MITM Phishing Attack
It's pretty long, but his is the main point.
codes generated by Google Authenticator (OTP) are specific to the destination site. However, since the user has to submit this manually, then there is room for human error. If we can somehow remove the human in the process and have the application submit the code only for the intended destination, then this would be more secure.
U2F and Security Keys
If the human is the biggest vulnerability in a phishing attack, then we should just remove the human in the process.
This is what U2F tries to do. We relieve the human the burden of identifying between fake and real sites. This is going to be taken care of by the YubiKey and the browser working together.
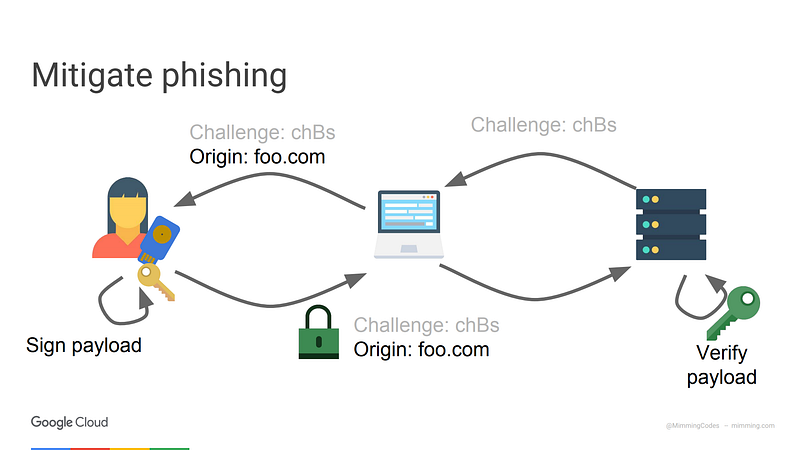
If you look at the diagram below, we see a desirable end to end flow, and for the most part, this happens automatically end to end. In U2F, whenever the security key generates an authentication code, it is partly derived from the identity of the destination.
See also https://www.perplexity.ai/search/are-webauthn-passkeys-unfishab-9QJZb8e1QceeixauGJutaQ#0
Core security properties
Both U2F and WebAuthn/passkeys use per‑site public‑key pairs, so a key registered for one origin cannot be used to authenticate another origin, preventing classic phishing site credential reuse.
The private key never leaves the authenticator (security key, TPM, Secure Enclave, etc.), so there is no shared secret for an attacker to steal or trick the user into disclosing.
Phishing resistance is achieved because the browser/OS includes the real origin in the signed data; a fake domain gets a different challenge context, so the signature is useless to the attacker.
See also Passkeys and the future of modern authentication | Yubico